If 2025 taught Canadian businesses anything, it’s that cyber threats aren’t just a global conversation anymore, they’re showing up in our own communities. Airlines, retailers, small towns, school boards… the list grew longer each month and whether you’re running a five-person operation or managing a wider IT footprint, those headlines felt uncomfortably familiar. They nudged you to ask the quiet question many leaders avoided saying aloud: Would our defences hold if someone tested them tonight?
Let’s walk through what happened last year and, more importantly, what these moments say about the year ahead.
Here’s a quick snapshot of the six major cyber headlines that shaped the conversation in 2025
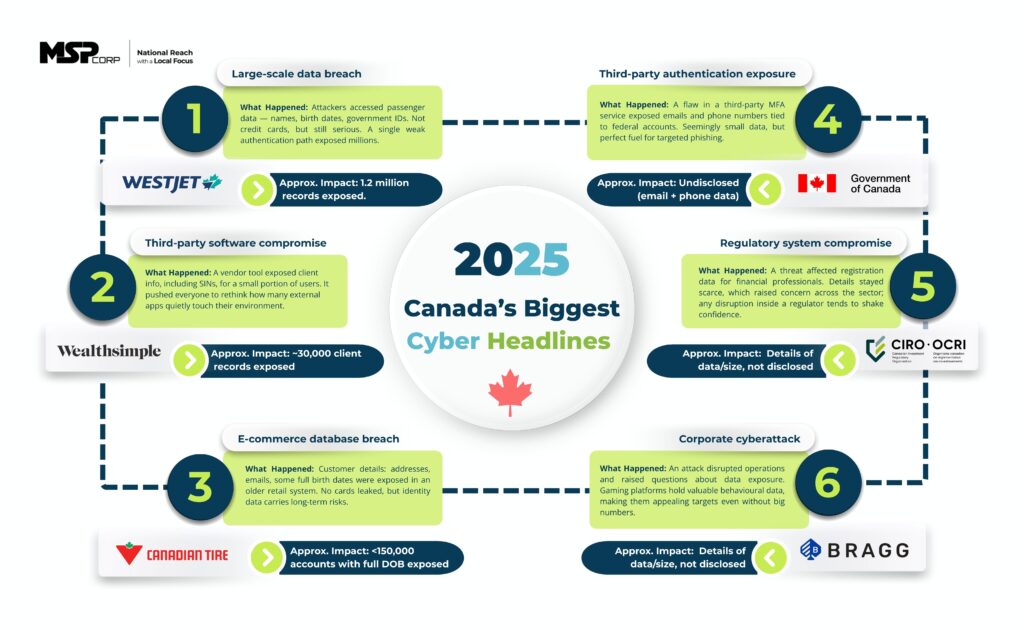
Notable Cyber Incidents That Shaped Canada in 2025
1) WestJet Airlines | Large-scale identity exposure
On June 13, 2025, WestJet discovered unusual activity across systems tied to booking data and internal operations. The airline later confirmed a “sophisticated criminal third party” gained unauthorised access in a publicly posted security notice. Independent reporting estimates the incident affected around 1.2 million passenger records, including names, dates of birth, government IDs and travel document details. While payment card numbers and passwords were not exposed, the combination of identity and travel data still carries significant long-term fraud and impersonation risk.
Approximate impact: ~1.2 million passengers
Lesson: Identity and travel data can be just as damaging as financial data; assuming “non-payment” systems are safer is a costly mistake.
2) Wealthsimple | Third-party software compromise
On August 30, 2025, Wealthsimple discovered that a trusted third-party software package had been compromised. In its public security update, the company explained that fewer than 1% of its clients were affected, which translates to roughly 30,000 people. For those clients, the exposed data included SINs, dates of birth, contact information and government ID details, though no accounts or funds were accessed. The incident was contained quickly, and affected users were offered credit monitoring, but it still raised hard questions about how far a vendor’s security reaches into a customer’s life.
Approximate impact: ~30,000 clients
Lesson: Your security posture extends well beyond your own codebase; every integrated vendor tool quietly becomes part of your attack surface.
3) Canadian Tire Corporation | E-commerce database exposure
On October 2, 2025, Canadian Tire Corporation reported a breach in an e-commerce database that supports banners such as Canadian Tire, SportChek, Mark’s and PartyCity. In its public disclosure, the company confirmed that customer names, emails, mailing addresses and years of birth were accessed, and that for fewer than 150,000 accounts, full dates of birth were also exposed. Passwords were encrypted and card numbers were truncated so they could not be used for purchases, and no banking or loyalty systems were involved. Even so, the presence of identity data in an older web platform showed how quietly these “supporting” systems can turn into prime targets.
Approximate impact: <150,000 accounts with full DOB exposed
Lesson: When multiple brands and legacy web systems intersect, the forgotten e-commerce database is often the weakest and most attractive entry point.
4) Government of Canada (MFA Provider Incident) | Authentication data exposure
Between August 3 and August 15, 2025, a flaw in a third-party multi-factor authentication provider led to exposure of contact information linked to federal user accounts. The government noted in its official statement that emails and phone numbers tied to CRA, ESDC and CBSA users were accessed. While no financial data or credentials were involved, contact information alone is enough to supercharge tailored phishing campaigns. Many security teams recognized a familiar lesson here: even trusted authentication layers can introduce risk when visibility into third-party vulnerabilities is limited.
Approximate impact: Undisclosed (emails + phone numbers)
Lesson: “Low-risk” data such as emails and phone numbers often becomes the first domino in high-impact attacks when paired with social engineering.
5) CIRO | Registry system compromise
On August 11, 2025, CIRO confirmed it had detected a cybersecurity threat affecting registration information connected to member firms and thousands of registered investment professionals. The organization acknowledged the incident in a public CIRO notice, and further communication revealed that affected individuals were offered two years of credit-monitoring and identity protection. While CIRO did not disclose the full scope of exposed data, the decision to activate identity-protection services suggested the risk extended beyond basic contact information. For many in the financial sector, this hit close to home: a regulator’s compromise can undermine confidence across an entire ecosystem.
Approximate impact: Not disclosed
Lesson: When oversight bodies experience instability, it sends shockwaves through every organization that depends on their authority and integrity.
6) Bragg Gaming Group | Behavioural and transactional data risk
On August 8, 2025, Bragg Gaming reported a cyberattack affecting its internal systems. Public reporting listed the incident among Canada’s national cyber events for the year. Though Bragg did not publish a detailed breakdown, the concern centered around potential exposure of behavioural and transaction-related user data. Gaming platforms hold complex identity footprints, everything from account details to patterns of activity, which makes them attractive to attackers even when conventional financial data isn’t explicitly involved.
Approximate impact: Not disclosed
Lesson: Attackers increasingly seek behavioural data, not just payment records, because it can be weaponized across multiple attack paths.
Quick Hits: Four More Incidents That Still Matter
Even without large disclosures, these incidents shaped conversations across Canada:
- Town of Devon (Alberta): Ransomware disrupted key public services.
Lesson: Small IT teams in public service environments often carry the heaviest load. - Limestone District School Board: A cyber incident paused school operations across multiple sites.
Lesson: Education systems hold sensitive data but rarely have matching defences. - Brunswick Health Group (QC): Patient information was accessed.
Lesson: Healthcare breaches cut deeper because they impact both privacy and care delivery. - Colabor Group Inc: Ransomware slowed supply-chain operations and delivery timelines.
Lesson: In distribution environments, every hour of downtime has a price tag.
What These Incidents Tell Us About 2026
When you look across these incidents, a clear pattern begins to surface. None of them started with dramatic intrusions. Instead, they slipped in through ordinary places, such as older systems that had gone untouched for too long, vendor tools that suddenly behaved in unexpected ways, or authentication layers everyone assumed were locked down. The common thread is that everyday complexity has quietly become the real vulnerability.
This matters for 2026 because every new connection, whether hybrid work access, SaaS integrations, mobile logins or cross-platform identity tools, introduces another point where small cracks form. Attackers are no longer hunting for full financial records. They increasingly target emails, phone numbers and behavioural fragments, which AI can turn into convincing impersonation attempts. Smaller teams and public-sector groups feel this more intensely, not due to carelessness, but because limited staffing and older technology create openings that are hard to close.
Security in the coming year will be shaped less by major breaches and more by these quieter, relational threats that take advantage of overlooked systems and the assumptions people make about trusted providers.
A practical way forward begins with visibility, meaning a clear sense of which apps, integrations and authentication tools your team relies on. Once you see the full picture, the real risks become easier to spot. Often, it is not the obvious systems but the forgotten ones that end up creating the biggest gaps. From there, identity management becomes the anchor: who has access, from which device, and under what conditions. Tools like conditional access, trusted-device rules and strong MFA may not feel glamorous, yet they consistently stop incidents before they escalate.
Organizations using Microsoft 365 already have many of the protections they need, including Defender, Intune, Purview and secure Copilot controls. The real challenge is weaving them together in a way that fits how people work. That is where a partner becomes valuable. Internal teams rarely have the time to follow every access path or reconfigure older setups. MSP Corp helps fill those gaps through co-managed IT, Guardian Shield MDR and modern workplace governance.
Ultimately, the stories from 2025 aren’t warnings so much as reminders. They show that even large, well-resourced organizations can be caught off guard, and that smaller teams can come out the other side when they have the right support and preparation. Security doesn’t need to feel heavy or intimidating, and it certainly doesn’t have to be something you navigate on your own. If any of these incidents sparked questions about your own environment or you’re simply looking for a clearer path into 2026, our team is here to help. Reach us any time at cybersecurity@mspcorp.ca, and we’ll walk you through the next steps in a way that fits your systems, your priorities and the way your team works.

